codes and ciphers
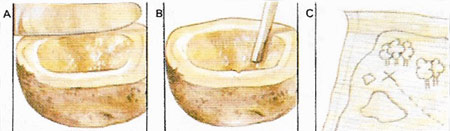
Figure 1. Secret ink can be made from many substances ranging from potato juice to the most sophisticated chemical compounds. To make a potato inkwell, scoop out the center of a potato and scrape juice into the hole (A). A message written with this juice (B) will be invisible, but can be read when the paper is heated to 120°C (248°F) (C). If paper is waxed by rubbing it with a candle and laid waxed face down on plain paper, then a message written on the plain paper will be impressed as a waxen line and become legible after powdered coffee, soot, or some other dark dust has been scattered on to it.

Figure 2. A simple transposition of the letters of a plain-text message (A) is achieved by writing it in rows (C) beneath a code word, in this case "SPECTRUM" (B). The letters of the code word are numbered according to their position in the alphabet (for SPECTRUM it is CEMPRSTU) (D). Then the message is written in the order of the numbered columns (E). To decipher, you need only know the code word.
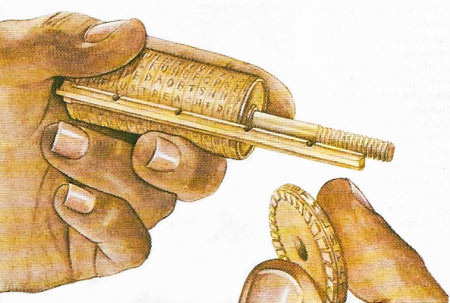
Figure 3. Thomas Jefferson (1743–1826) devised a wheel cipher consisting of 36 wheels that can be assembled in any order. Upon each of them the letters of the alphabet are written in jumbled order and the number of different combinations this gives amounts to many millions. It was by far the most advanced cipher of its day and was adopted by the American army almost at once. It is the basis of some modern machines.
Many ways of concealing messages exist, but basically the plain-text can be disguised in two ways. The first is by steganography, which conceals the message's very existence by writing it in invisible ink (Figure 1), or reducing it either to a microdot about the size of a period (full stop) or to a micropulse. A message can also be arranged in such a way that the first or last latter of each word in an apparently innocuous text spells out a real message.
The second way to disguise plain-text is to transform it in to one of two ways. The first is by transposing the letters of the message in a prearranged order to make a cipher (Fig 2); the second is to substitute the letters of the plain-text by other letters, numbers, or symbols to form a code.
Forms of code
A code, as distinct from a cipher, involves the substitution of prearranged code words, code numbers, or code groups for words, phrases, or syllables. The trilingual international code in English, French, and Spanish invented by Marconi, for example, has five-letter groups representing common words in each language (UVYDU = railway sleeper, traverse, traviesa). The groups are recorded in a dictionary and were used to save telegram costs. This type of code can be secret or open, but military or diplomatic codes based on this principle have to be further disguised to make them secure. An example is the one-time pad code used by the British in World War II.
In this, to send the message "To the C-to-C; Tanks will move tomorrow at dawn", the sender looks up the basic code which contains a list of words and phrases commonly used in military operations, thus "To the C-to-C = 5475; Tanks will move = 9835; Tomorrow = 4439; At dawn = 7463". Since code books are liable to loss or capture, it would not be safe to send this message as 5475:9835:4439:7463. Frequent repetition of such phrases as "To C-to-C" would soon be identified and the code cracked. It is therefore necessary to disguise these four-figure groups. The safest way of doing this is for both sender and recipient to have what is known as a one-time pad on each page of which are columns of four-digit groups printed at random. The sender indicates the page, column, and line where the message is to start, thus: 1549, which would mean page 15, column 4, line 9. If the next four groups beginning on page 15, column 4, line 9 are 4431:7628:5016:4881, the code text to be sent (5475:9835:4439:7463) is written down and to each group are added the figures taken from the one-time pad, i.e.:
| 4431:7628:5016:4881 |
| 5475:9835:4439:7463 |
| _____________________________ |
| 1549:9906:7463:9455:2344 |
To decode, the recipient subtracts the one-time pad groups from the groups received; the refers to a code "dictionary".
Ciphers and secrecy
Simple substitution ciphers afford little protection since substituting one letter or symbol for one letter of plain-text reflects the frequency of letters occurring in the language.
To encipher the message "Tanks will move tomorrow at dawn" by a simple letter-for-letter substitution cipher based on the following key:
| Plain-text | abcdefghijklmnopqrstuvwxyz |
| Cipher-text | monseratbcdfghijklpqzyxwvu |
the result is as follows.
| Tanks will move tomorrow at dawn |
| qmhdp xbff giye qigillix mq smxh |
A further elaboration that helps disguise the letter frequencies is the bigrammatic Playfair system in which the message is first split up into groups of two letters regardless of word breaks and then changed according to the following rules. Letters of the alphabet are arranged in five columns of five letters each (I and J occupy one space), i.e.
| M | O | N | S | E |
| R | A | T | B | C |
| D | F | G | H | IJ |
| K | L | P | Q | U |
| V | W | X | Y | Z |
If the two letters of the groups form the diagonals of an imaginary square within the five columns, the letters at the opposite sides of the square are chosen (plain-text NK = cipher mp). If they are on the same line, then move one letter to the right (TA = bt). If they occur in the same column, then the letters immediately below are chosen (WA = of). To encipher "Tanks will move tomorrow at dawn" the letters are written out TA NK SW IL LM OV ET OM OR RO WA TD AW NX and the enciphered text will read: bt mp oy fu ko mw nc no ma am of rg fo tn.
An efficient way of preventing wire-tapping is to shift the frequency of the sounds of speech, or scramble. Time division scrambling (TDS) cuts the stream of speech into split-section portions and shuffles them by first tape recording the conversation and then picking off segments in jumbled order.


